Introduction
This Guide will point out the reasons and the solution on how to resolve an issue in OpenWrt where WireGuard seems to block traffic on other completely unassociated zones.
The Problem
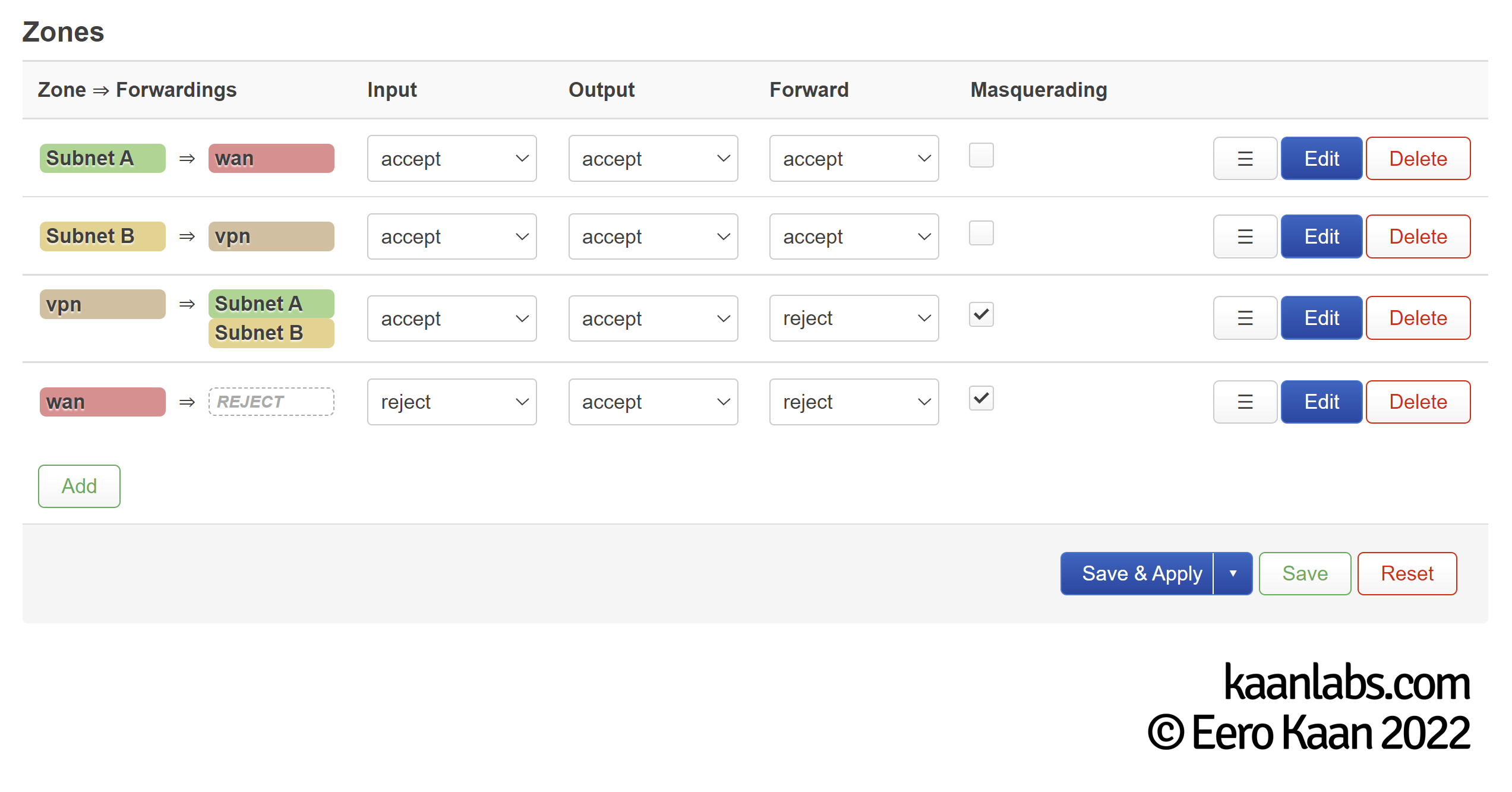
Assume you have two subnets on your OpenWrt router. Subnet A (192.168.10.0/24) routes directly to the WAN zone, whereas Subnet B (192.168.20.0/24) routes to a VPN zone powered by WireGuard. This firewall zone configuration incorporates the “kill-switch” method (i.e. traffic can not leave the internal network, for as long as the VPN is not active).
When the WireGuard interface is not active, you have no connection to internet on Subnet B and working internet on Subnet A – that’s fine and as expected.
However, things get weird when the WireGuard interface is active. This time, Subnet B has a working internet connection through the VPN – that’s good so far – but Subnet A now doesn’t have a working connection, even though Subnet A is completely uncorrelated with the WireGuard VPN interface. So what gives?
Whether it is active or not, the WireGuard interface acts as an IPv4 upstream gateway and as such, OpenWrt will try to force the traffic of Subnet A through there.
Logically it can’t because on the one hand the firewall doesn’t allow this flow of traffic and on the other hand, the WireGuard service is disabled on top of that. If the WireGuard interface is even configured to start on boot, it may even well be the default gateway.
The Solution
OpenWrt has to know which subnet goes to which interface, based on metadata (the affected subnets / address range) we have to define first. This is called policy based routing.
Step 1: Fixing WireGuards Boot-Time weirdness
But first off, we have to take care of a weird behavior of the WireGuard implementation on OpenWrt first. WireGuard shouldn’t be allowed to start on boot, as it may block any further traffic necessary in the power-up phase. Instead, set up a NTP Hotplug to start up the WireGuard interface on boot. Fortunately, I have already encountered this oddity before and wrote a guide on how to fix this: Fix broken WireGuard Connection after OpenWrt Reboot.
Simply create the 90-wireguard config file as shown in the guide and continue here to implement the aforementioned policy based routing.
Step 2: Setting up VPN Routing Policies
For OpenWrt to know which zone refers to the WAN and which one to the VPN gateway, proceed to install the vpn-policy-routing and the luci-app-vpn-policy-routing opkg packages under “System > Software“. Reboot your router now.
Now onto the main attraction: Setting up the policies. Go to “VPN > VPN Policy Routing” and create the policies which suit your network. For the given network example (the one described under the “The Problem” section), the policies would look like this:
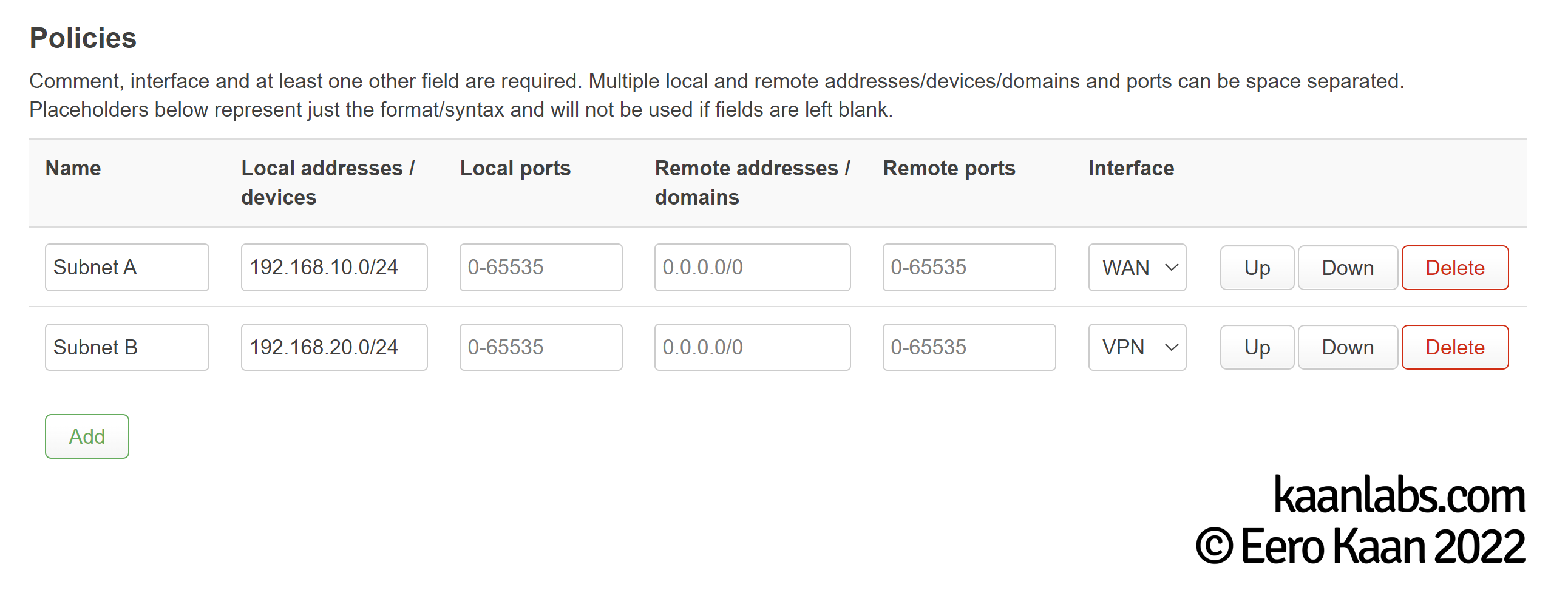
Finally, enable the Routing Service by clicking on “Enable” and on “Start”. Now reboot your router again.
That’s it. OpenWrt should now route Subnet A always directly to WAN, whereas Subnet B always goes its way through the VPN.


